Although We often rely on MAC adress filter to prevent unauthorised users from accessing a wireless LAN, MAC addresses can be easily spoofed. Thios project is on spoofing your own PC's MAC adress.
Step: 1 Open a web browser and go to
www.klcconsulting.net/smac. A web page will open up like the following-

Step: 2 Click to download Smac 2.0.
Step: 3 Under evolution edition, click free. this will install the free version of the software.
Step: 4 click download now and the download will begin.
Step: 5 When the file downlaod dialog box appears click save and follow the instructions to save it in a place of your choice. after saving, click on run and follow the instructions to install the program.
Step: 6 Click Finish to launch the application and accept the licence agreement.
Step: 7 You'll be prompted for a registration id.

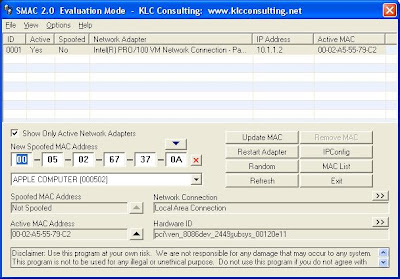
Click proceed and the application will be started. Smac discovers your network adapter card and displays it.

Step: 8 Click on the network adapter to change the MAC adress.
Step: 9 Record the current MAC address under active MAC. Which was in my case, 00-02-A5-55-79-C2.

Step: 10 Click the random button to create a new2 MAC adress.
Step: 11 Click the update MAC button and then click yes.

You will see that the active MAC address has been changed to the new one.

Step: 12 Reboot your computer.
Step:13 Lets verify that the MAC address has been changed. Open command prompt by clicking Start>Run and typing in "cmd" then press enter.

Step: 14 In the command prompt, type "ipconfig/all" and press Enter. The New MAC address will appear.

Step: 15 To re-enable your original MAC address, launch SMACand click Remove MAC.
 Make sure that, the active MAC address is your original one.
Make sure that, the active MAC address is your original one.
Step: 16 Reboot your computer.
Case Project 6.3 Detecting a wireless access point
Rogue wireless access point is one of the most critical security concerns of IT managers today. (Gier,2003). Amongst all other wireless security concerns few are as dengerous as rogue wireless access point. (Pacchiano, 2006).
There are many ways to track down a rogue wireless access point. One of the cheapest and cost effective way is to manually track it down, which can be very time consuming, specially if you are doing it for a very large company. The following steps will get you through the processes-
Step: 1 You need to install a wireless sniffing tool. (e.g. Netstumbler or AirMagnet) in your laptop or pda. I personally recomend Netstumblert as it is very good at detecting all wireless networks within a broadcast area and is free to download from the company's website http://www.netstumbler.com/downloads/
Step: 2 After installation you'll need to walk every where within your network and catch wireless signals.
Step: 3The simplest way, is to take the laptop (which is running Netstumler) and walk in the direction that produces the greatest signal from a questionable access point.
Step: 4 Doing this, you'll soon be able to get whether the signal is coming from within your building or from outside.
Step: 5 If it is coming from your building, keep doing what you've been doing. Which means keep walking to a direction to get stronger signal.
Step: 6 You should be able to narrow down your search to a single room soon.
Step: 7 After that, you just have to hunt down the room to discover the wireless access point.
How to compare any discovered AP's against those AP's that are approved?
Very simple. Just compare the MAC addresses. If the discovered MAC adress is not in the list, this has high potential to be a rogue wireless access point. However, this is not always the case. For example, once a team of network experts were trying to setup a new access point in a small office. While the Manger was trying to establish a connection between his laptop and the new access point, a DHCP server from a nearby office assigned an IP adress to that system. Was that a rogue acess point? ofcourse not. So, sometimes you'll also need to use common sense to help distinguish between a non-threat neighbouriong access point from a serious threat, and trust me this will save you plenty of headaches. (Pacchiano, 2006).
References:
1. Gier, Jim. (January 6, 2003). Identifying rogue access point. Retrieved January 29, 2010 from http://www.wi-fiplanet.com/tutorials/article.php/1564431
2. Pacchiano, Ronald. (March 10, 2006). How to track down rogue wireless access points. Retrieved January 29, 2010 from http://www.smallbusinesscomputing.com/webmaster/article.php/3590656
No comments:
Post a Comment