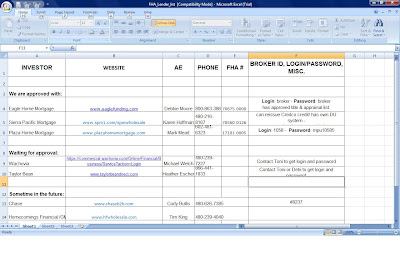
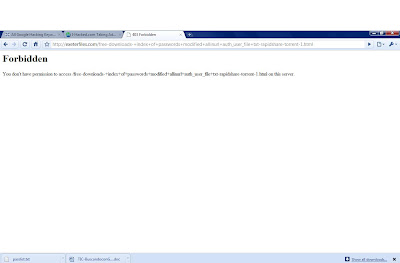
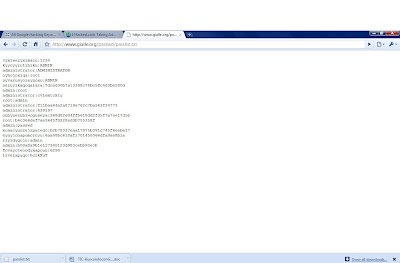
Keylogger is aprogram that captures everything that a user enters on a computer keyboard. The program runs invisibly in the background and cannot be detected by normal users even from the Windows Task manager, as it is not shown in the application tab. However, it is possible for advanced user or computer experts to detect it from the processes tab though it is hard to find out.
The purpose of this activity is to provide information regarding how these programs function in order that adequate defenses can be designed and implemented. The steps to follow are the followings:
Step:1|| Open your web browser and enter the URL www.softdd.com/keystrokerecorder/index.html.
Step:2|| Click download here.
Step:3|| When the file download dialog box appears, click save and follow the instructions to save this file in a location such as your desktop or a folder designated by your instructor. When the download has been finished click run and follow the default installation process. Note that, some anti-virus software may detect that this program is a malware. It might be needed to temporarily disable the antivirus software in order to download and run the application. It is highly recomended though that, you turn the antivirus software back on once this assignment is finished.
Step:4|| click run keyboard collector and then click ok. when asked for a password click ok. The keyboad collector settings are as below.
Step: 5|| Select the always run checkbox.
Step:6|| click Activate/Start and then click Yes to confirm.
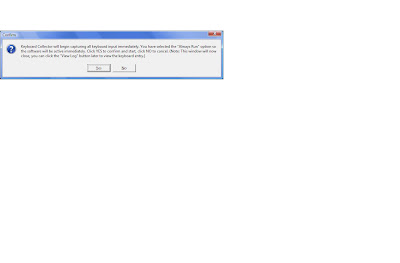
Step: 7|| Spend several minutes performing normal activities like creating a text document.
Step: 8|| Now examine what keylogger has captured. double click the Keyboard Collector Trial on desktop.
Step: 9|| When asked to enter a password click ok.
Step: 10|| click Run Keyboard Collector and then click ok.
Step: 11|| click view your logs and then click ok. Notice that the text you've typed has been captured.
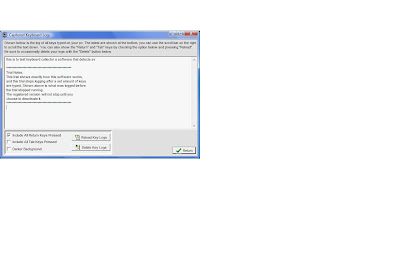
Step: 12|| click
Return and then
Exit.
Step: 13|| Now notice that keyboard collector is cloaking itself so that it does not appear to be running. Press the ctrl+alt+del keys and click Start task Manager.
step: 14|| Click the application tab to see all the programs that are running at the moment.
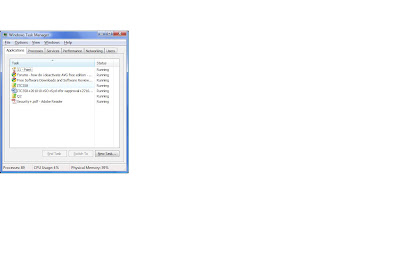
Note that, Keylogger is not shown in the list. This kind of malwares work behind the screen so normal user cannot detect them and doesn't come to know that they are affected. They hide themselves from the Task Manager's application tab, however, it is possible to detect them if you go through every single processes that are running from the processes tab.
How to install keylogger in a computer for which you dont have a user name or password?
The best way of doing it would be sending e-mails with the virus attached to it. once the email is opened and downloaded the program will be automatically installed in that computer.
References:
1. Security+ guide to Network Security Fundamentals, Third edition, by Mark Ciampa. page: 31-33.
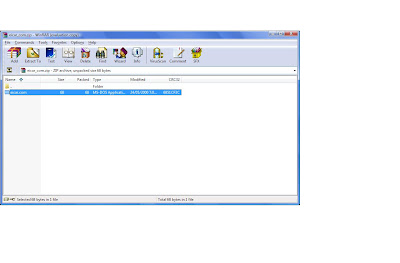 Step :8-12|| These steps are unnecessary in my case, as my norton anti virus stopped me from opening the content. and showed this message.
Step :8-12|| These steps are unnecessary in my case, as my norton anti virus stopped me from opening the content. and showed this message. Step: 13|| Return to the web site and this time click eicarcom2.zip. This is a double compressed zip file with a fake virus.
Step: 13|| Return to the web site and this time click eicarcom2.zip. This is a double compressed zip file with a fake virus. 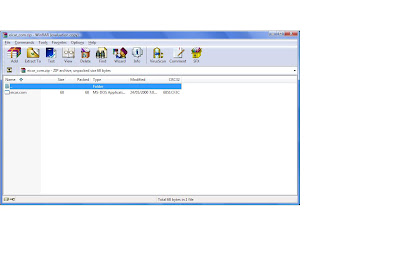 Double click on eicar.com. My norton anti virus software protects me from the virus and shows this message.
Double click on eicar.com. My norton anti virus software protects me from the virus and shows this message.